What is IKEv2 VPN? Features and How It Works
With the increasing need for security and privacy in the online space, users are seeking solutions to protect their information. One of the popular and efficient protocols in this area is IKEv2 (Internet Key Exchange version 2). In this article, we will examine the features, advantages, and how IKEv2 VPN operates.
- What is IKEv2 VPN?
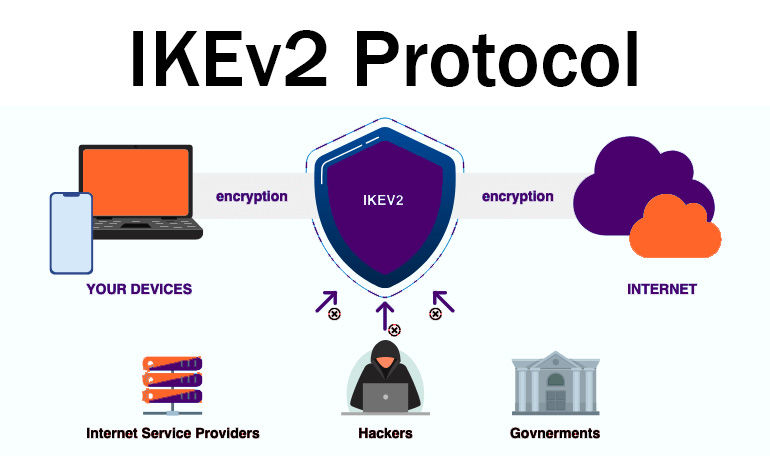
IKEv2 is a VPN protocol designed to create secure connections between users and VPN servers. This protocol operates as part of the IPSec (Internet Protocol Security) suite. In other words, IKEv2 helps devices communicate securely with each other. Due to its high speed and reliability, this protocol is commonly used in modern VPN networks. Additionally, IKEv2 has improvements in performance and security compared to its predecessor, IKEv1, and can easily adapt to network changes (such as IP address changes). Overall, IKEv2 is a key tool for securing online communications and protecting data during transmission. This protocol combines with IPSec because IPSec is known for its security and reliability, while IKEv2 stands out for its speed and exceptional stability, especially when a quick reconnection is necessary. These features are very useful during network changes or sudden disconnections; therefore, the combination of IKEv2 and IPSec creates one of the best VPN protocols that leverages the strengths of both technologies. Furthermore, IPSec creates secure tunnels between two points (peers) that communicate with each other and is used for encrypting data in VPNs.
- Features of IKEv2 VPN
1. High Speed: IKEv2 has high data transfer speeds due to optimization techniques. This feature is particularly important for users interested in streaming and online gaming.
2. Strong Security: This protocol uses advanced encryption to protect user information from cyberattacks. IKEv2 supports AES and 3DES encryption algorithms, ensuring high security.
3. Stability: IKEv2 adapts well to network changes. For example, if a user switches from Wi-Fi to a mobile network, the VPN connection remains established automatically.
4. Multi-Platform Support: This protocol is usable on various operating systems such as Windows, Mac, Android, and iOS.
5. Ease of Use: IKEv2 has simple settings that users can easily configure.
- Advantages of Using IKEv2 VPN
Privacy Protection: By using IKEv2 VPN, your real IP address is hidden, and your information is protected from government surveillance and hackers.
Bypassing Restrictions: This protocol allows users to access blocked content in different geographical areas.
Improved User Experience: The high speed and stability of IKEv2 provide users with a seamless experience in streaming and web browsing.
- How IKEv2 VPN Works
IKEv2 operates like any other tunneling protocol, establishing a secure connection between the VPN client and the server. This link is created only after authenticating the client and server with a private key, followed by setting data exchange rules. Additionally, IKEv2 manages the features of Security Associations (SA). In other words, it establishes security features between the VPN client and the VPN server. Both parties must use the same settings for successful data exchanges, resulting in the generation of a shared symmetric encryption key. This key is used at the end of each exchange after the data has passed through the VPN tunnel.
In other words, the operation of IKEv2 VPN involves the following steps:
1. Establishing Connection: The user connects to the server using their VPN software.
2. Key Exchange: At this stage, the necessary information for encrypting data is exchanged between the user and the server.
3. Data Encryption: After establishing the connection, the user’s data is encrypted to ensure its security.
4. Data Transmission: The encrypted information is transmitted to the server, and after processing, the requested information is sent back to the user.
5. Receiving Information: The user views the received information without concern about intrusion or surveillance.
- Comparison of IKEv2 with Other Protocols
IKEv2 has specific advantages compared to other VPN protocols like OpenVPN and PPTP:
Speed: IKEv2 is generally faster than PPTP and even OpenVPN in certain conditions.
Security: While PPTP offers lower security, IKEv2 provides high security using advanced algorithms.
Stability: IKEv2 adapts well to network changes, while some protocols may struggle in this regard.
Conclusion
IKEv2 VPN is one of the best options for users looking to maintain their online privacy and security. With high speed, strong security, and ease of use, this protocol can provide an exceptional user experience. If you are also looking for a reliable solution to protect your information, IKEv2 VPN will be a suitable choice for you.